Cryptography has become a very important part of the security of information that people share. It has been in use for many years, from the kings to send messages to now having great importance on the internet.
Symmetric Encryption and Asymmetric Encryption are both a type of cryptography.
They both are used in daily life. Big examples include: when one needs to send a confidential email, or one is doing electronic banking online and even some apps and servers.
There are many examples, and one needs to have proper information before choosing a particular Encryption that they want to go through with.
Key Takeaways
- Symmetric encryption uses the same key for both data encryption and decryption, while asymmetric encryption uses different keys for encryption and decryption.
- In symmetric encryption, the security of the data depends on the protection of the key. In contrast, in asymmetric encryption, the safety of the data depends on the complexity of the algorithm used to generate the keys.
- Symmetric encryption is faster and more efficient for encrypting large amounts of data, while asymmetric encryption is more secure for transmitting data over insecure channels.
Symmetric Encryption vs Asymmetric Encryption
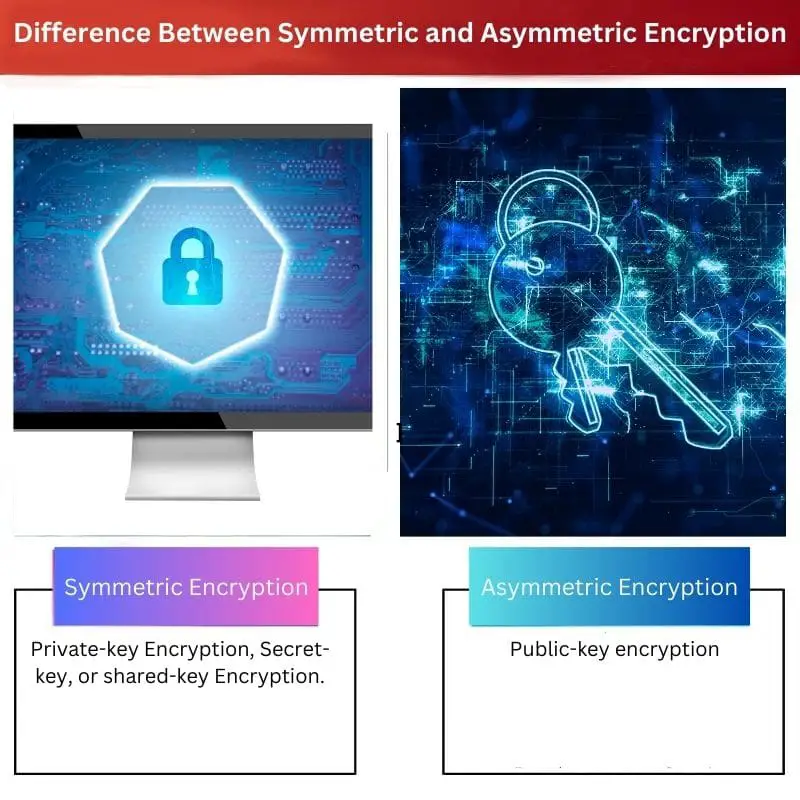
Symmetric encryption is a type of encryption in which the same keys are used for encryption and decryption. It is a fast encryption process. It only uses private keys. In asymmetric encryption, different keys are used for the encryption and decryption. Private and public keys can be used in asymmetric encryption. It is a secure process.
Symmetric Encryption is a type of Encryption that uses only a single set of keys to encrypt and decrypt. The Caesar Cipher is one of the earliest examples of this Encryption.
It includes five steps: writing the plaintext, encryption using an algorithm, using the private key, processing into the Ciphertext, and decrypting the message.
Asymmetric Encryption is a type of Encryption where two types of keys are used: A public key to encrypt the data and a private key used for decrypting the data. This is quite a slow process since it requires two keys, but side-by-side is also a securer process.
Comparison Table
| Parameters of Comparison | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Other names | Private-key Encryption, Secret-key, or shared-key Encryption. | Public-key encryption |
| Number of keys | Only private keys are used. | Uses both private and public keys. |
| Time consumed | The process of Symmetric Encryption is fast. | In comparison to Symmetric Encryption, it is slower. |
| Security | Asymmetric Encryption is less secure. | More secure than the process of Symmetric Encryption |
| Examples | Blowfish, AES, RC4, and many more. | DSA, and RSA, and many more. |
What is Symmetric Encryption?
Symmetric Encryption is a form of encryption. They use certain algorithms in the process. It is also popularly known as”Secret Key” Encryption since they need to protect the key from third-party individuals.
Symmetric Encryption has the biggest advantage of being fast and efficient for the users. The rate per bit of key is quite fast. The main disadvantage this process has is that the sender and the receiver have to have mutual trust between them as they will use the same key to open the information.
The Symmetric Encryption process is far older than all the other Encryption techniques available nowadays, including Asymmetric Encryption.
The biggest disadvantage that the process of symmetric Encryption has is the sharing of keys. Ideally, the key is already shared between the parties ahead of the message sent and received.

What is Asymmetric Encryption?
Asymmetric Encryption is a process that is used in cryptography. It is used to encrypt and decrypt data with the help of “keys.” A single key could be described as a string or collection of alphabets and numbers that are stored in a file.
The process of Encryption and decryption can not be completed without these.
It is also called public key Encryption, and it is becoming increasingly popular these days, mainly because, unlike Symmetric Encryption has a downfall in the distribution of keys, in this process of Asymmetric Encryption, there is no problem with the sharing of keys.
The algorithms used in the procedure of Asymmetric Encryption are complex. The reason being it uses both a private key and a public key. The public key is used while encryption is disclosed, but the key that is needed for decryption, the private key, is confidential and is only with particular clients.

Main Differences Between Symmetric And Asymmetric Encryption
- Symmetric Encryption uses a single set of keys, while in comparison, that is called private keys. Asymmetric Encryption uses different sets of keys, a public key and a private key, used by the sender and the recipient, respectively.
- Symmetric Encryption is faster than the process of Asymmetric Encryption as Asymmetric Encryption uses two different sets of keys, and Symmetric Encryption uses the same set. The keys used in the Symmetric Encryption process are shorter than those used in Asymmetric Encryption.
- Asymmetric Encryption is more secure than the process of Symmetric Encryption as it has less chance of getting attacked as only particular individuals know the key to decrypt the data or the information.
- Symmetric Encryption is used when one needs to transfer a larger amount of information, while Asymmetric Encryption s used when the information is small in number. It is because Asymmetric Encryption uses a larger period of time to encrypt and decrypt.
- Symmetric Encryption is used for the encryption and decryption of data for a longer period of time, starting from 100 BC. In contrast, Asymmetric Encryption came up much later. Thus, making the process of Symmetric Encryption older.
- https://books.google.co.in/books?id=fzoiOeUf8fIC&printsec=frontcover&dq=symmetric+and+asymmetric+encryption&hl=en&sa=X&ved=2ahUKEwiswobhzsfwAhXGT30KHTrYC0QQ6AEwA3oECAMQAw#v=onepage&q=symmetric%20and%20asymmetric%20encryption&f=false
- https://ieeexplore.ieee.org/abstract/document/8308215

A great resource for anyone seeking to grasp the intricacies of encryption methods.
Yes, the article effectively explains the nuances of symmetric and asymmetric encryption.
The explanation of how symmetric and asymmetric encryption work is very well done. It’s an insightful read.
Yes, the article delves deep into the specifics of each encryption method.
Absolutely, the detail provided here is impressive.
This article is a great educational tool for understanding how encryption works and the different variations available.
Definitely, the key takeaways and comparison table are particularly useful.
I appreciate the depth of detail in explaining both symmetric and asymmetric encryption methods.
The breakdown provided here makes it much easier to understand the complex aspects of symmetric and asymmetric encryption.
Precisely, the article is great at simplifying complex encryption concepts.
Agreed, the comparison table helps to highlight the main differences between the two methods.
This article does a fantastic job at breaking down the complexities of both symmetric and asymmetric encryption methods.
Absolutely, the description of how each method works is very clear and easy to understand.
Great article! This is an incredible comparison between symmetric and asymmetric encryption.
Yes, I couldn’t agree more. It’s so detailed and informative.
This article has been incredibly informative. I’ve learned a lot about encryption from reading it.
The clear explanation provided here makes it easier to understand the differences between symmetric and asymmetric encryption.
Yes, the comparisons provided are very helpful and insightful.
Absolutely, this article is a fantastic resource for those needing to understand these concepts.
I’ve been looking for a comprehensive article on encryption, and this one is just what I needed.
Definitely, this article provides a thorough understanding of encryption methods.
This article provides a comprehensive overview of symmetric and asymmetric encryption methods. Great read!
I agree, the level of detail in this article is truly beneficial.