Privacy concerns are more relevant than ever in today’s interconnected world. Sharing your phone number with strangers, businesses, or untrusted entities can lead to spam calls, scams, or even privacy …

Welcome to our Computer Networks category page! This is the hub for all things related to networking. We offer a comprehensive collection of articles, tutorials, and resources that cover a wide range of topics, including network design, configuration, troubleshooting, and security. Our content is designed to cater to beginners and experts in the field, providing valuable insights and knowledge to help you achieve your networking goals. Explore our different sections, filter by category or skill level, and enhance your network skills today!

Privacy concerns are more relevant than ever in today’s interconnected world. Sharing your phone number with strangers, businesses, or untrusted entities can lead to spam calls, scams, or even privacy …

WhatsApp is a convenient platform for communication, but its popularity has also made it a target for scammers. These scams are becoming increasingly sophisticated, often involving international calls, fraudulent messages, …
What are IP Addresses? An IP address, or Internet Protocol address, is a unique identifier for every device connected to the Internet. It consists of a sequence of numbers separated …

Why Dynata Calls You? Dynata is a market research company conducting surveys and gathering data on products and services. They may call you because they want your opinion on various …

What is WPS Button? The WPS button on your router stands for Wi-Fi Protected Setup. It is a feature designed to make setting up a secure Wi-Fi connection more straightforward …
Experiencing the minor inconvenience of forgetting your WiFi password can leave you puzzled, especially when you need to connect a new gadget or share network access with guests. Fortunately, retrieving …

Navigating the digital pathways of your home network brings you to gateways critical for device communication. The IP address 169.254.1.1 stands as a gateway to your router’s administrative interface. Renowned …

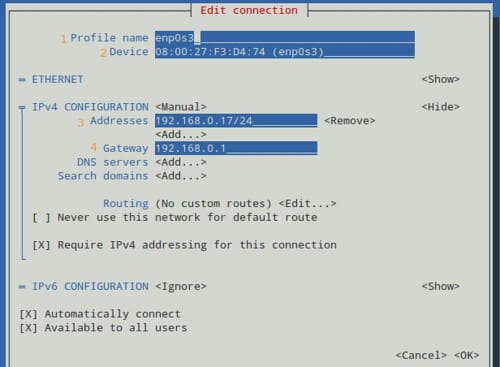
Accessing your router’s admin page is essential for managing your home network settings. To reach this interface, simply enter ‘192.168.1.1’ into your web browser’s address bar. This particular IP address …
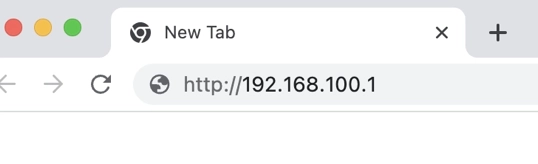
Steps for Logging into 192.168.100.1 In order to configure your router, you’ll need to access its interface via the IP address 192.168.100.1. Below are the necessary steps for a successful …

Managing your router effectively is essential for maintaining a secure and functional home or office network. To customize settings like Wi-Fi passwords, parental controls, or device permissions, you’ll need access …
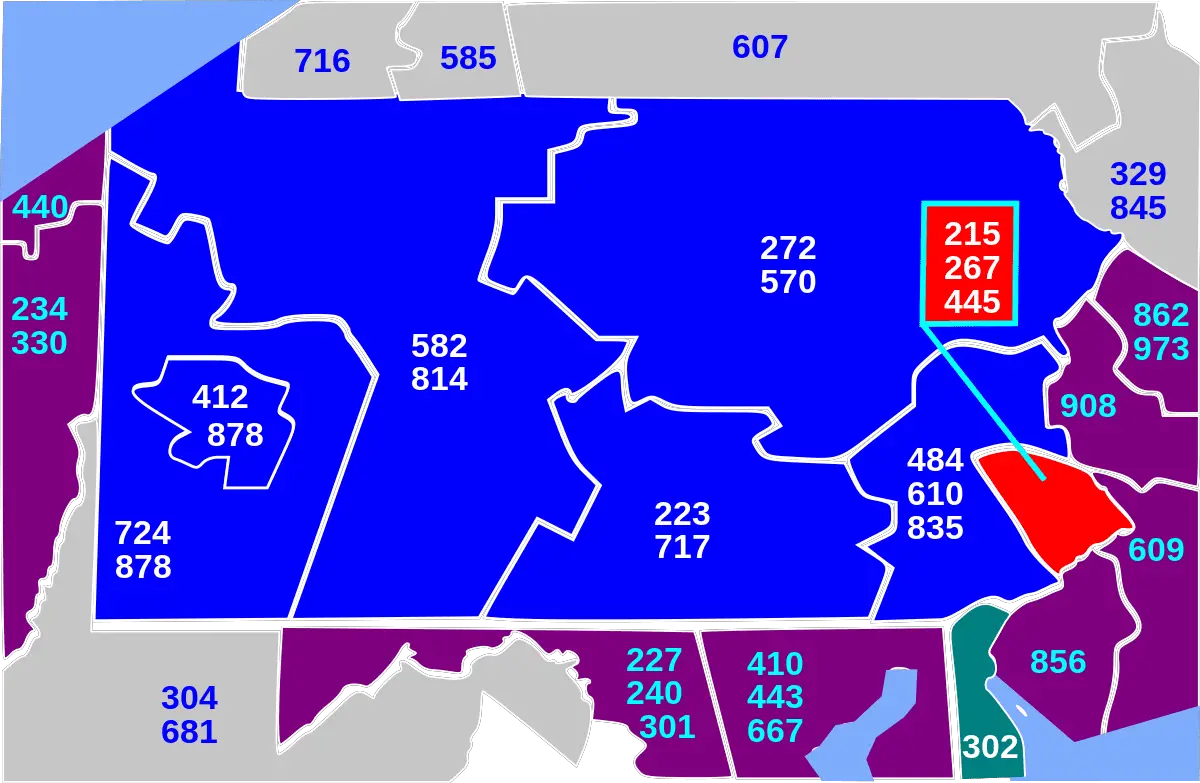
What are Area Codes? Area codes are crucial to telephone numbers in many countries, including the United States and Canada. The three-digit prefixes help route your call to the right …

What is Google Fi? Google Fi is a mobile virtual network carrier (MVNO) that offers voice calling, SMS, and mobile broadband services. Originally known as Project Fi, it was launched …

Definition of SMS SMS, or Short Message Service, is a communication technology that allows you to send and receive text messages on your mobile phone. It is a component of …

Requirements to Access Comcast Business Router Login Before you access your Comcast Business Router login, ensure you have the requirements for seamless connectivity. Following these steps will allow for a …

ATTWiFiManager Login To access the ATTWiFiManager, first, connect your device to your AT&T hotspot’s Wi-Fi network. Once connected, open a web browser on your device and enter the following URL …

Steps to Spectrum Router Login Accessing the Admin Panel To access the admin panel of your Spectrum router, you need to be connected to your network via WiFi or with …
AT&T Router Login Procedure To log into your AT&T router, follow these simple steps: Once successfully logged in, you can explore the various settings and options available to customize your …
CenturyLink Router Login Basics You might need to access your CenturyLink router for various reasons, such as changing the WiFi password, modifying the settings, or updating the firmware. This section …

Prerequisites of Att.Wirelessinternet Login Before you attempt to log in to your AT&T Wireless Internet account, you should have prepared a few key things to access your account seamlessly. Following …
How to Login to Xfinity Router To log in to your Xfinity router, follow these simple steps: To ensure a convenient experience, consider the following tips: Once you successfully log …

Asus Router Login To access and customize various settings for your home network, you must log in to your Asus router. Here’s how you can log in: If you have …
NETGEAR Router Login You must log in to its web interface to access and manage your NETGEAR router. Here are the steps to follow: Once you have successfully logged in, …

Myfiosgateway.com Myfiosgateway.com is a web portal that allows you to access and manage your Verizon FiOS Quantum Gateway router settings. By logging into Myfiosgateway.com, you can change your Wi-Fi name …

5GHz WiFi Your Samsung TV may support 5GHz WiFi, depending on the model. To connect, follow these steps: Remember that some Samsung TVs only support 2.4GHz networks, so check your …

What is NFC? NFC is the abbreviation used for the term Near Field Communication. This technology was developed where two devices can communicate wirelessly at a distance of up to …

What is Bluetooth? Bluetooth is the wireless technology that stormed the tech market, allowing two different devices to connect at short distances. This technology was developed by Ericsson in 1994, …

What is Gateway? In an operating systems interconnection (OSI), the element that operates on all seven layers is known as a gateway. It is also considered a protocol converter as …

What is an eSim? An embedded sim or eSim is an electronic form of a sim card that can be inserted into a cell phone without physically purchasing it. It …
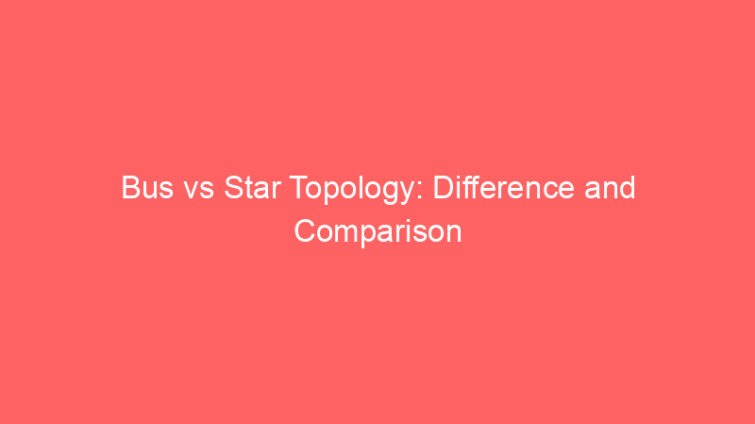
What is a Bus Topology? Bus topology is the network topology in which all the devices are connected by one single cable, known as the backbone cable, and all the …

What is Broadband? Broadband refers to a high-speed Internet connection that allows for fast data transmission. Unlike dial-up connections, which use a telephone line to connect to the Internet, broadband …

What is Bluetooth? Bluetooth is a wireless technology used for short-range communication between devices. It is commonly used for wireless audio streaming between devices such as smartphones, speakers, and headphones …
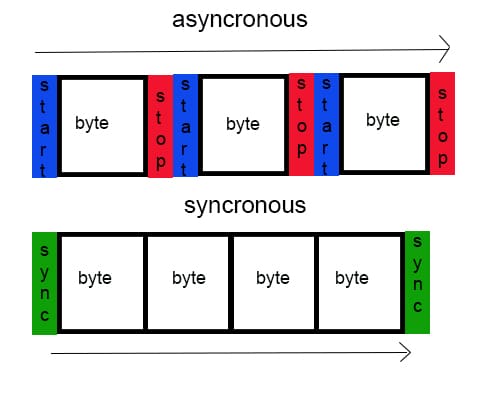
What is Synchronous Transmission? Synchronous transmission is a transmission method in which data is transferred as a continuous stream of signals. In this method of transmission, data is transmitted at …
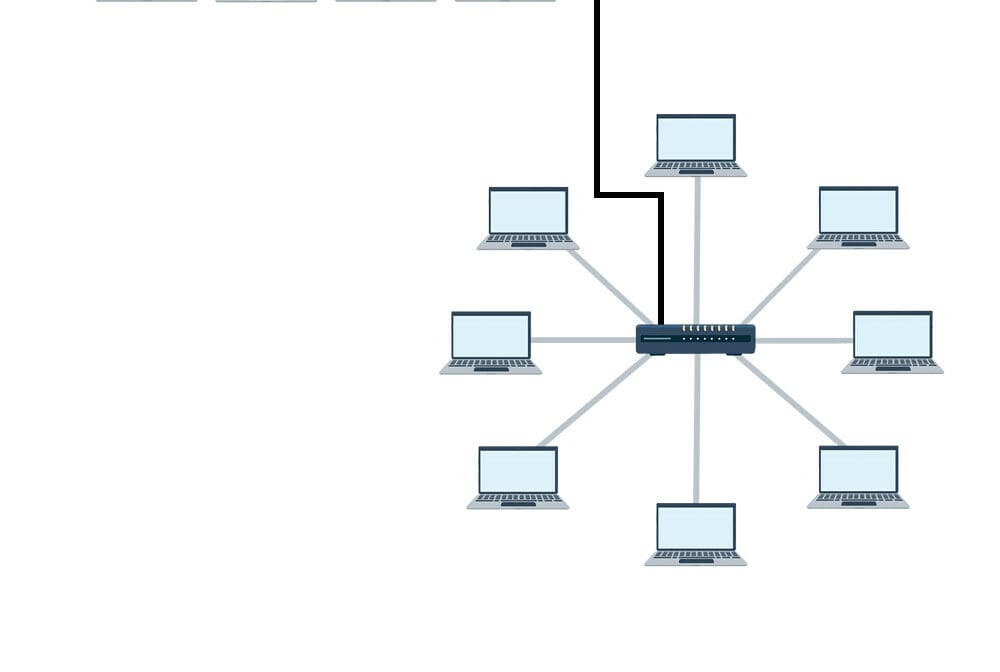
A star topology is a type of network topology in which all devices are connected to a central hub or switch. A ring topology is a type of network topology …
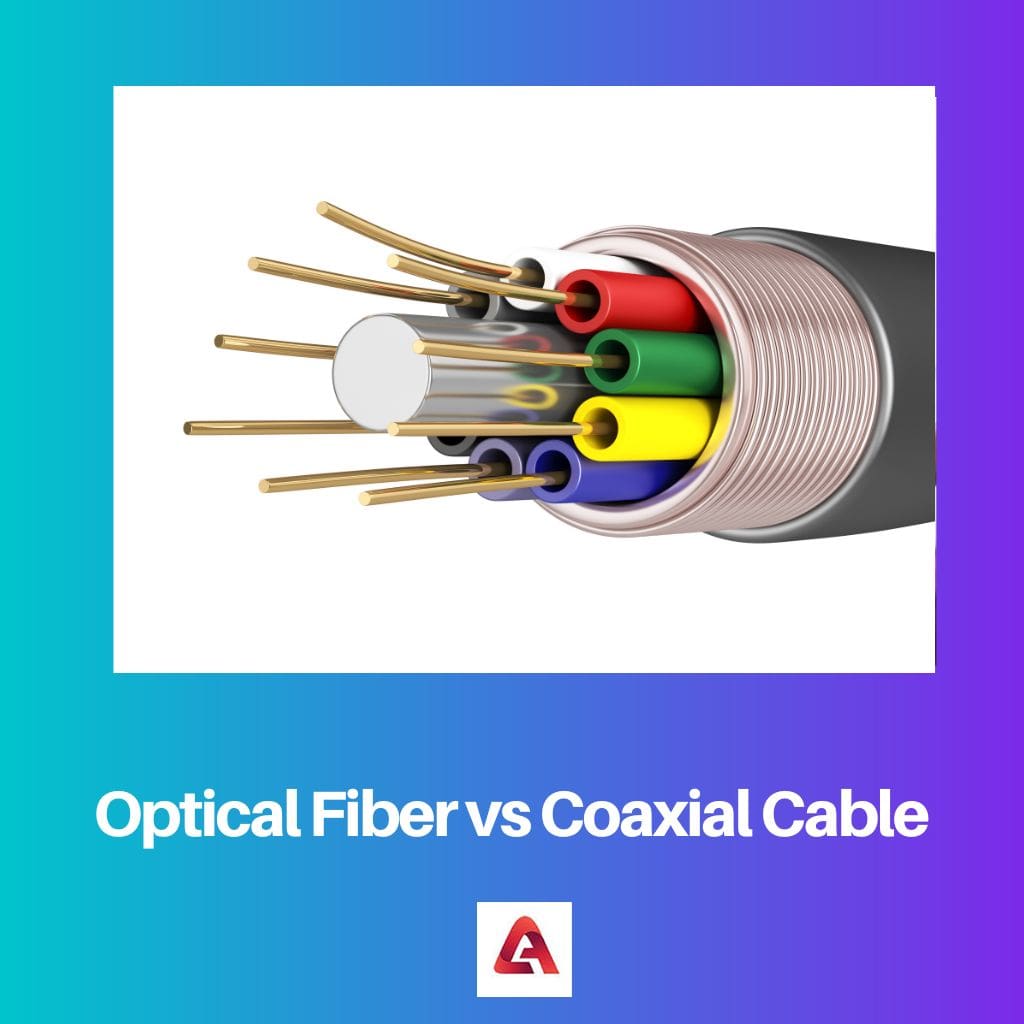
Optical fiber is a type of cable made of fibers that transmit light signals over long distances. Coaxial cable consists of a copper wire surrounded by an insulating layer, woven …

What is Serial Communication? Serial communication is a process in the field of telecommunication and data transmission. Here the data that is subjected to be transmitted goes sequentially, one bit …
Telecommunication is advancing every day, with wireless communication at the top of the charts. WiMAX and ZigBee are two essential, emerging, and commonly used wireless communication technologies that are continuously …

In this world of developing technology, telecom operators, i.e., networks, are essential for communication, and some of the enormous telecom operators are – Vodafone and ‘Jio’. Even though they belong …
Site-to-site and remote access enables users to access information that is not ordinarily available to them. Both services are utilized in business transactions, allowing employees to acquire data from the …
Modern society revolves around the infinite chain of computer networks. Whether it’s banking or taking classes, everything is part of a computer network, or it would be more accurate to …
Computers changed human lives. Our lives have been made easy with technology and computers. Internet improved the application of computers. Several computers are connected to form a network. Networking helps …
A computer is the result of several devices assembled together. But there are devices that are not in-built but have to be connected to a computer. That’s when computer networks …
The devices that connect networks and create interaction between two devices are known as the networking devices. There are various types of network building. The activities of communication are carried …
The internet and mobile phones are inextricably linked. Mobile phones that do not have network connectivity capabilities are unfit for the twenty-first century. Airtel and Jio, two mobile rival network …
The lifespan of an allocated IP address is the gap between a static as well as a dynamic IP address. Usually, a static IP address is directly allocated to a …
As everything is going online, why won’t the office? There are online platforms that provide video conferencing workstream collaboration platforms for organizations. To take your office online, there are many …
Not all routers are made perfect when it comes to offering fast and stable WiFi signals. Even though the new WiFi’s are causing numerous transitions to the new consumer networking …
The internet is a public network; therefore, it is open for all, and hence it is also a place for several types of malware software. The Intranet and VPN are …
GRPS and 3G is the most up-to-date technology, supporting fast transmission speed that is a 2G standard, whereas 3G is a 4G standard. Moreover, just like GRPS, 3G offers two-way …
The Internet is a network of different computers and computing devices. The network is made by connecting different computing devices in a grid, where information can be passed on from …
Despite the importance of the internet in our everyday life, starting from GPS to office work, very few know the intricacies that lie behind the router box. There exist several …

In the past 20 years, computers have increased in the market at a very fast pace and owing to this shift in technology, many companies have constantly been competing with …
Google Fi, earlier called Project Fi, is a telecommunication service provided by Google that provides calls, SMS, and versatile broadband utilizing cell organizations and Wi-Fi. Google Voice is a telephone …
Certain software allows everyone to submit their comments and ideas about their projects and work, making it easy to interact with your coworkers and share your ideas. Cisco Jabber and …
The Internet has become one of the most important things in our lives an individual daily work and activities will completely stop if there is no internet connection. There is …
Bandwidth is a term used to describe the amount of data transported. The term “bandwidth” refers to the amount of data that may be sent in a given amount of …
Google is best known for providing useful applications and services to internet users. Some of their features like the Google assistant are fun and innovative. These types of innovations let …
The world of the Internet comes with various advantages as well as disadvantages. There are threats and dangers wrapped in every data, whether incoming or outgoing. Every network has two …
We have lost the daily interaction with team members, co-workers and that’s when video and audio meetings came to the rescue which would help us to interact with team members …
Due to increased usage of the internet, our data may be threatened by hackers and that results in unwanted scams and advertisements which may hinder our work while on the …
Everyone wants the right cabling for their applications and researching the right cabling is a must. In today’s time, the use of Ethernet for networks has become very common. All …

In this internet world, our devices are becoming more vulnerable to malicious software. We work with different devices and different secondary storage devices. And we also visit different websites for …
With the increasing technological advancements, the Internet has become an indispensable part of our lives. It serves several practical functions in one’s life such as helping us in accessing news …
We are quite familiar with the term ‘Interface.’ We all do have a basic and minimum knowledge about its function and working. In simple words, it refers to a medium …

When computers had just stepped into the world of the internet, there was only one computer that would connect to the modem at a time. But with the advancement of …
WEP shares are a type of wireless network security protocol. You must enter a passphrase and provide a key that can be shared between the client and the access point. …
The way of listening and consuming music has revolutionized with Internet accessibility. Various platforms have been launched to provide distinct features for audio streaming. The two most popular music streaming …

With everything shifting to the online mode, choosing the most appropriate Wifi for the house has become all the more essential. Choosing one that does not fluctuate and serves your …
Technology is an ever-developing field. We carry the world in our pockets, and all it takes is a few taps on our cellular device. Google Voice and RingCentral are two …
Networking is one of the basic practices to maintain our social life, the exchange of ideas occurs as a result of networking. It allows us to connect with people from …
In an increasingly globalized world that is powered by the latest technologies, it is impossible to stay out of the space called the internet. The internet has been in the …
Many companies provide virtual phone systems to people across the world. Such services are associated with cloud computing. These phone services are very beneficial to call worldwide. Google Voice and …
WDS implies a Wireless Distribution System that allows network access without utilizing wires. The devices connect wirelessly with each other. The WDS devices operate as WDS Relay or WDS Remote. …

Today hacking has become an act that happens very frequently. Small to big, every kind of data can be easily leaked or infected by a hacker if not widely protected. …
Mac address and IP address are two search terms that have been very commonly discussed and addressed from time to time but still, there exists confusion between these two terms …
The concept of voice over Internet Protocol is becoming popular day by day across many parts of the world, and eventually, people are opting for this technology due to numerous …
The IT sector has seen exponential development on its horizon. The acceptance of cloud networking deploys greater challenges in maintaining agility and security over the cloud. To address these issues …

Cisco Jabber and IP Communicator are two distinct terms with distinct significance. Individuals’ virtual lives are made easier by the presence of this incredible technology. Cisco Jabber and IP Communicator …
If one router is unable to give appropriate Wi-Fi service to every area of your home, mesh network solutions and distance extenders are excellent solutions to boost Wi-Fi signal and …
A local area network is a cluster of network endpoints that communicate with one another. Similarly, a VLAN is a sort of LAN that expands on the possibilities of a …
Prevalent in different parts of the world, there are certain technologies that aid in achieving access to multiple network channels at once, and CDMA and GSM happen to be with …

There are many wireless technology options to choose from, which makes it tough for people to choose the right access control system according to someone’s needs and preferences. RFID and …
In the internet era, there are hundreds of devices are used to circulate information or data from one place to another. The easier this procedure seems, the more complex the …
Efforts to improve data communication technologies are primarily concerned with ease & convenience. We prefer to interact with others with as little effort as possible. We may now send and …
A Demilitarized Zone, or DMZ, is a smaller component of a larger openly accessible network to the public and the internet as a whole. Port forwarding is a type of …
A PBX, also known as a unified communications system or a business phone system, serves as a fundamental central controller for calls within a company. Internal traffic between stations is …
Since hackers are not leaving any stone unturned in stealing critical information from the internet (websites, mobile applications) by infecting them with a virus, data security is becoming the topmost priority …
In this era of generation, people might be living far away from their loved ones and their family members. People need to connect and talk with their friends or anyone …
The network has made our life so easy that now we can connect to anyone no matter where they live and can share our data like photos, videos, and other …
For installing a wireless fidelity network in the entire building (houses, workplaces, restaurants), certain network technologies could be embedded along with the wife router. Access Points and Mesh are the …
AWS makes connecting your on-premises system to the cloud architecture relatively simple. One of the most effective methods is to take advantage of already existing connectivity, that is, the Internet. …
Cisco offers two different service tiers for businesses seeking to operate an IT network: Network Essentials and Advantage. Network Essentials is a simple but powerful offering that provides baseline networking …
Zeno and Zeno Hot Spot are portable electrical devices that use heat to kill acne bacteria. Zeno is the brand name for all Zeno acne treatments, whereas Zeno Hot Spot …
SNT and SNTP are services provided by Cisco. Cisco is a California-based worldwide software corporation. Cisco is a vital provider to Silicon Valley’s growth by developing, manufacturing, and distributing networking …
Studying networks in computer science is very important. Without the knowledge of computer networks, people cannot understand how computers work and the connection behind them. The two essential connection protocols …
Microsoft NPS and Cisco ISE is a cloud-based networking service that allows for easier implementation of network access control, both within an organization and by allowing access to outside resources. …
For many organizations, such as businesses and universities, it is exceptionally essential to invest in firewall solutions such as Cisco ASA and Palo Alto, which is a great next-generation firewall. …
When it comes to routing is the process of path selection network traffic or across or between multiple networks. It can be performed in several network types: computer networks (like …
Security and privacy are very important elements of the digital world we live in. Whether cloud security, computer security, password protection of online accounts,s or digital locking, all are equally …
There seem to be presented four alternatives for Cisco contact center portals: Unified Contact Center Xpress (UCCX), Unified Contact Center Enterprise (UCCE), Packaged Contact Center Enterprises (PCCE), and Webinar Contact …
With advancements in technology, most household tasks have also been digitized. Be it printers, PCs, or televisions, everything is a necessity now. Furthermore, there are times when connecting these devices …
As the use of technology is increasing daily, crimes against these technologies are also growing at the same rate. To be safe from these threats, extra protection is required in …
The most basic definition of a router is that it connects two more networks. A router routes the IP addresses to route the package and is responsible for path determination. …
NAC is a Cisco product used to identify and evaluate hosts that attempt to connect to your network (especially before they have access). ISE is an application that provides various …
Physical protocols of information are pivotal in today’s technology-driven era. They are necessary to ensure that data transmission takes place following certain standards. RS 232 and RS 485 are two …
The internet is a very important and crucial part of everyone’s life. The GLC-T and GLC-TE both are the equipment that ensures that a high-speed connection can be provided in …

Wibree and Bluetooth are wireless connection technology for transferring files or data. The primary reason for introducing Wibree and Bluetooth technology is to overcome the large cables. Both of them …
The radio is the technology that helps transmit messages worldwide using frequency. Radio waves are used in radio. Before televisions were introduced, radio was top-rated among the people. The cricket …
The speed at which data is produced daily is good and evil. While all this data is made sometimes, we must also send data from one point to another. To …
When it comes to email handling protocols, there is a variety to choose from. SMTP and MAPI are two of these protocols. Microsoft designs MAPI, and SMTP is designed by …
Microsoft Remote Desktop Services (RDS) and Citrix are two popular options for Virtual Desktop Infrastructure (VDI). Both are cloud-based services that allow access to application resources from any device remotely. …
CISCO is a public networking hardware and software industry founded on December 10, 1984. With its headquarters in California, CISCO forms the core reason behind the growth of Silicon Valley. …
Cisco Webex is a well-known American company that makes money by selling video and web conferencing software. Webex now includes several new capabilities that are equivalent to those found in …
Hub and Bridge are two computer networking devices that allow regulating data to the other related devices. Both devices are used for different purposes, and they also work differently. Hubs …

Bluetooth was introduced in 1998, and to date, it is an in-built feature in almost every android, iOS, and another device. We examine the various Bluetooth versions and how they …
In modern times, the internet has become a powerful resource of information. Without the internet, a person can’t lead a normal life. Everyone is engaged with the internet in some …
Internet connectivity is a crucial criterion in the global economy. The speed of the internet plays a pivotal role, and most of us depend on it. The emails, images, and …
The CISCO Clientless SSL VPN creates a remote access VPN tunnel without requiring the installation of any hardware or software VPN client to provide access to a corporate network. AnyConnect …
Regarding network communication, the setup of the physical layer is a process known as switching. Switching means when multiple communicating devices are connected. There are two types of switching. The …
A computer network is a set of many connecting devices through links. There are many tasks which computers have to perform. So there are many network devices. And networks are …
Redundancy protocols are necessary for a technical environment operating on a computer network. It helps identify how the routers are connecting to transfer or distribute the information between the various …
HSPA, or High-Speed packet access, refers to third-generation technology for mobile broadband. It mainly consists of two protocols that are used in tandem, known as HSDPA and HSUPA. HSDPA refers …
Cisco is a networking company with offices across the world and a headquarter in the United States. It makes multiple hardware and software devices that it sells to customers. This …
The field of the internet is constantly expanding. People are becoming more active on the internet in modern society. The Internet is a virtual Home for countless information provided by …
Both VPN and Remote Desktop are boons of modern technology, but their functions are completely different. They are not the same thing. Their security, purpose, and procedures of working are …
The second and third-generation wireless communication technologies are referred to as 2G and 3G, respectively. The growing need for communication in the modern age has resulted in a series of …
LTE (Long Term Evolution) is a fourth-generation communication from the third-generation [project 3GPP. The LTE has got a 10ms frame of duration with 10 subframes. The subframes have two specific …
In today’s world, many internet users perceive Wi-Fi and broadband connections to be the same technology. However, it is critical to understand that the purposes and properties of these terms are distinct. …
The airport extreme and the airport expresses are the devices or routers for internet access wirelessly that the Apple company creates for gadgets like mobile phones, laptops, or desktops with …
Wireless connectivity with different devices is at the forefront of technological advancements in the 21st century. The ability to connect with millions of devices from around the world is a …
In the world of growing digital presence, the technology of exchanging data has evolved too. When discussing data exchange, The two most common technologies that come to our mind are …
The network is required to connect various servers across the world. Therefore, they help people all around the world to connect. This is the reason that the architecture of the …
Cisco offers AP in various modes. The modes can operate in lightweight or even autonomous versions, depending upon the need and image for which it runs. Most of the customers …
Mark Spencer (Founder of Asterisk) created the IAX standard to address some of the shortcomings of the SIP standard. Later, an improved edition of IAX, known as IAX2, was released. …
In the networking world, different types of protocols are used to transfer data. The Internet transfer Protocol, known as IP/TCP, is used in all communication protocols, whether the Internet or …
Hubs and switches are examples of networking equipment that fulfil different tasks in an Ethernet network at different levels. Even if they are occasionally combined into a single device, the …
GBIC and SFP are transceivers that can be used as optical transmission receiver devices use to connect to motherboards. This helps interconversion between electrical and optical signals, as every transceiver …
A bridge and switch is a device that keeps track of signal flow and data transfer inside a network. Switch only sends data to the device that requests it, rather …
Keeping your computer, privacy, and important documents safe by protecting them against malware (such as computer viruses, worms, spyware, botnet software, and ransomware) and giving virus removal tools. Malware is …
Over the last decade, data centres have quickly increased server virtualization, dramatically advancing agility and flexibility. It is easier to monitor, automate, and orchestrate a network that has been virtualized …
Cisco Jabber and Webex have exceptional importance in businesses and organizations of all types, including government, education, healthcare, and financial institutions. Cisco Jabber is designed for conferencing, in-person meetings, and …
Emails are very important as it holds important information. In today’s world, thousands of emails are sent everywhere. Email security has become very important. Email security is something where various …
Microsoft DirectAccess and VPN are two technologies that are very popular among IT professionals. Each of them is used to access intranet connectivity through the internet. They are mistakenly confused …
Technology has revolutionized every industry and taken the world’s future on a different road. This also includes the Internet and the world wide web, which have helped millions of people …
Both the terms cisco jabber and Yammer are used for private communications within an organization. They facilitate secure communication with clients or any other external group related to an organization. …
Nowadays, knowledge has become data, and this point can not get stretched enough, but in our lifestyle, we are always required to stay virtually connected. And this uninterrupted connectivity with …
When it comes to communication, texting has surpassed phone calls. The first, SMS, is at the forefront of messaging. However, many people prefer comparable services such as BBM or Blackberry …

At present, recruitment companies look after the skills of their hiring individuals. For fulfilling the same perspective, many companies also offer free or paid certification courses for students to pursue. …
Mobile communication technologies have evolved with GSM (Global System for Mobile Communication) and 3G (3rd Generation mobile technology). The use of multiple access technologies makes GSM and 3G devices capable …
Routers and transistors have been in use since the explosive growth of technology. Along with them came another gadget that helps transmit wavelengths of information and data. It was called …
Both the Firewall and the Proxy server are a barrier to control the traffic which resides between the network and the local computer. They provide security against network threats. The …
Cisco C9200 Series Switches and Cisco C9300 Series Switches are both LAN switches designed for corporate networking. Cisco Catalyst 9200 model Switches are intended to accommodate corporate branches with little …
Gateways and firewalls could be classified as system security or network stabilizing unit that allows communication between multiple networks. They allow pre-monitored interaction between the desired and authorized users to …

With Medianet auto-configuration and media monitoring features, their cameras would begin broadcasting footage seconds after already being linked. Two such cameras are the Cisco Quad camera and P60. Cisco Quad …
Various network protocols connect people with technology via the internet. The IP address and the ethernet networks vary in internet access. DHCP and PPPoE are the two kinds of protocols …
These days when we talk about mobile, it’s moreover calls or messages in the present scenario. The very first thing for which mobile has become a necessity is just for …
Forescout CounterAct is a network access control (NAC) device similar to Cisco ISE. FS queries network components using SNMP as well as SSH to identify and characterize associated destinations. FS …
Today, there is development in every field. From science to medicine, nothing is left behind. In this era where most things are done on the internet, communications are also developed …
Cisco Systems Inc. is a company specializing in communications and networking products and services. Cisco issues various certification programs to provide trained professionals to solve consumers’ problems related to its …
Cisco is the leading network equipment industry and provides a varied range of network solutions. Cisco DNA and ACI are technical terms, and people get confused with their configuration. DNA …
Cisco Small Business RV Series Routers include virtual private networking (VPN) technology, which allows remote workers to link to your network via a secure Internet connection. Operate your network with …
If one is to say that this is the world of technology and we are living in it, it won’t be an exaggerating comment upon today’s scenario. It is almost …
The term ‘Power over Ethernet’ (PoE) refers to a means of providing data and power together to PDs (Powered Devices) with the help of Ethernet cables. In this, Ethernet cables …
Every computing device has a unique address to communicate with other devices on the distributed network. The nodes of the network have a unique address that is combined with the …
The third generation aims for the technology of telecommunications of wireless mobile. It is the upgrade for 2.75G and 2.5G GPRS networks for data transfer at a faster rate. It …

The Cisco ASR/AMRS system supports using two different security keys for any given operation: an unsecured key (0x7f4) and a secured one. The NCS 4000 bridges the gap between the …
Cisco ISE and Aruba Clear-Pass are Network access tools. They provide various services in network security and IT security. Both are available in different versions. Both of them have excellent …
With increasing workload and networking connections across multiple clouds, advanced security management is required to prevent threats and attacks. Here, we’ll discuss two types of secure network analytics that promote …

Fibre optics, also known as optical fibre, is an innovation that sends data as light pulses across a glass or plastic fibre. The number of glass fibres in a fibre …
Wireless internet connections have been doing the rounds recently. With numerous plans to attract users, these services have become the new normal. Since the billing is done monthly or yearly, …
Remote desktop enables the use of a desktop computer remotely. Users can connect and use a distant computer and access the files of the system using a remote desktop. Users …
Firewall Software and hardware protect computers from hackers and other online dangers by preventing harmful data from entering the system. Although hardware firewalls protect the network from external dangers, software …
3G cellular technology became immensely popular among the masses when it was released. It also paved the way for the following technological generations. UMTS and HSDPA are both 3G telecommunication …
A VPN (Virtual Private Network) increases a private network’s functionality, security, and management. It allows the users to establish a secured network connection while using a public network. The Cisco …
Cisco Hunt Group and Pickup Groups are communication features used by platforms for delivering or distributing calls automatically or manually by the user. These groups help decipher the call’s recipient …
Networking functions on different hardware. Hardware mainly includes routers. Routers have evolved and have launched as wireless routers. Linksys routers are the most popular routing devices which have several models …
Cisco Software Support Service offers great services to Cisco ONE for users. SWSS offers support services throughout the year and maintenance services. It has various tools and many other services, …
Cisco has location-based services for different purposes. One of them is Cisco DNA spaces and CMX. Both are location-based services that allow location analytics, troubleshooting, and managing networks. However, several …
Hyper-converged infrastructure (HCI) integrates computation, virtualization, storage, and networking in a specific group. Virtualized computing, software-defined storage, and virtualized networking are all part of HCI. COTS (commercial off-the-shelf) servers are …
Internet connectivity is a revolutionizing factor around which the entire world revolves. Every connection has certain parameters which the customers evaluate before installation. The two most common and popular data …
Cisco has been a pioneer in the industry of networking software, hardware and various other technical services and products for many years. The company has launched video conferencing systems that …
The term ‘email protocol’ stands for a standard way to exchange information between email service providers (like Outlook, Gmail, etc.) and email clients (like Apple Mail, Thunderbird) and vice versa. …
Many tools are used for distributing information; the first tool that comes to mind is the Internet. The advantage of the internet is not hidden from anyone, it is the …
They both the LAN (Local Area Network), which are part of the 9000 series of Cisco. They are known as hardware and software integrating innovations. They are switches, wireless controllers, …
It is a new norm for apps to be hosted on the cloud rather than traditional data centres. For this, cloud-delivered security is an important aspect that must be taken …
EIGRP and OSPF are two of the protocols with interior gateway routing. They help in selecting the routers for sharing and transferring the data through the interaction of routers. They …
Cisco DHCP Relay and IP Helper are the terms related to the Cisco routers. Their configuration differs as to which one we can enable and disable. They are the two …
The Cisco Webex and Skype are something that most companies choose to explore as they decide which program to buy and use as the main conferencing system. Cisco Webex is …
The world has digitalized, and communication has switched to wireless forms. Every device that we use is equipped with wireless capabilities. The two most important wireless forms in every device …
When it comes to networking, Cisco is one of the most well-known companies. Its constantly improving switches, routers, and advanced software enable it to meet today’s growing demands. Cisco Gibraltar …
Google fi is a project introduced by Google that provides the user with the facility of telecommunication, sending messages, and mobile broadcasts with the help of cellular data or wifi. …
The Cisco Networking Academy is part of the Cisco Learning Network, where students can learn about computer networking and Cisco products. Cisco CML and VIRL are lab environments. Students and …
Large-scale network connections create a lot of traffic between the links. Hence it is important to observe some protocols while establishing connections between different networks for the smooth operation of …
Mobile networks and communication have evolved technology over the past years to the point that it is now an everyday commodity. The demand for high-speed internet and data has increased …
Coaxial cable refers to an inner conductor enclosed by an insulating layer, which is enclosed by conductive shielding. Many cables also comprise an insulating outer jacket. This type of cable …
Registered jack is a telecommunication network that is used to connect local data and voice equipment to local or long-distance service. In this modern world, internet and voice connection is …

The platforms that enable online communication for video and audio meetings and seminars are known as video conferencing software. They have features like screen sharing, chatbot, and recording. This software …
Cisco is a leading networking and information technology company that connects computers that initiate data transmission to form connections over the internet. It develops networking hardware such as switches, routers, …
Firepower Threat Defense (FTD) operating systems are most popularly used in hardware platforms. FTD is also called Firepower NGFW. It is a next-generation firewall that provides an advanced VPN concentrator, …
A firewall is the basis of the network security of any organization. The job of any firewall is to build a security boundary between the networks and analyze internal and …
RJ45 and RS232 are two different types of connectors that are used for different purposes. RJ45 is the standard connector type for wired Ethernet networks, while RS232 is mainly used …
Rj11 and Rj12 are generic telecommunication network interface which connects long-distance or local exchange with voice and data communication. There are lots of registered jacks, and they are used for …
Cisco tar is part of the Cisco flash file system, however, there isn’t a single flash device on which we may store data. The bin file is a component of …
In today’s modern world, technology everything is almost everything online. And a good internet connection is not optional but mandatory. Different types of networking devices are used for the purpose …
Technology has improved so much nowadays that it is not even important to be in a place to see each other. This has led to making certain events easier. For …
Many corporations provide specific utilities to enhance the efficiency of the desired outcome. One of the major companies of the IT sector, Broadcom and Cisco, also provides specific functions for …
Because the amount of possible routes is relatively restricted, industry executives and engineers have predicted the eventual congestion of concurrent calls since the creation and marketing of cellular networks. RF …
DHCP, or Dynamic Host Configuration Mechanism, is a protocol for allocating free IP addresses to machines connected to a network. Static IP is not too complicated; it simply implies that …
With the growing technology, our dependency on it is also at an all-time high. Hence, Smartphones are a necessary modern-day need, and we need network services to use their full …
DNS and DHCP are two systems that are made up of client-server architecture. They are essential services in the IT network that are accessed every time a network-connected device is …
The advancement of technology in recent decades has been sans bound. With the leap of mankind towards artificial intelligence, various networking mechanisms were prone to make a breakthrough. Among many …
Routers are devices that form networks of computers or connect computers with the global internet. It is a device used to connect devices and connect them to the internet for …
When it comes to networks and their strengths, a large number of people are confused about the two terms VLANs and Subnet. It is very easily confusing as both are …
The multicast routing protocol has two versions: RSTP and PVST. Computers are the only ones that use the spanning-tree method. It guarantees a loop-free architecture and avoids bridge loops and …
Hyper-converged Infrastructure is a software-stipulated system. It combines all the functions carried out in a traditional data centre. These functions include storage, computing, networking, and management. Cisco HCI and Nutanix …
At this time, the industries are advancing towards the solutions which are cloud-based and networks that are Software-Defined; meanwhile, abundant vendors are leading the market with their unparalleled capabilities, features, …
Modern SIP (session initiation protocol) and IP phones are now connected via PBX systems. Voice over Internet Protocol and public switches are two ways to achieve the same goal: making …
Internet facility has changed the world. Our modern world is enhanced of facilities and communication only due to the blessing of the internet facility. Nowadays, everything is available at the …
Hashing methods are as safe as the mathematical function, but what counts later is the bit length, which should be as large as possible to avoid collisions (multiple inputs ending …
In the 1980s, Ethernet was developed to connect local devices in a region. It was called the Local Area Network. The purpose was to transmit and receive data from different …
Telephonic communication within a company, institution or any other office is very different from the local telephonic communication between houses in a city. With the special layout of telephone wires, …
The routing operations play a pivotal role in deciding the path and the sequence of the operation that is being performed. It can establish an optimum balance between the operations. …
Bridging is an important process in all network operating systems. It enables communication between interfaces that are connected to the network switch. Bridge group and bridge domain are two concepts …
We need modulation to transfer signals from one medium to another medium. These mediums can be either a physical medium or through any other medium. The two most modulations that …
Cisco has been a pioneer in the industry of networking software since the company was first set in motion. It has developed and deployed several systems that combine cutting-edge technology …
A VPN (virtual private network) is a one-of-a-kind technique of safeguarding privacy that works by connecting you to a single external IP address, preventing the outside world from determining where …
Next-generation firewall (NGFW) is a firewall technology of the third generation. It has features like DPI (Deep packet inspection) and IPS (Intrusion Packet System). The two main and common types …
Hackers are watching out for application weaknesses, which are, for the most part, found in feeble or taken certifications. Organizations are executing a few layers of safety to ensure their …
Connectors are equipment that serves as linkages between power lines for devices like phones and computers and internet sources like modems and routers. The RJ45 and RJ50 have a lot …
Cisco Systems’ Firepower Threat Defense (FTD) and Cisco Adaptive Security Appliance were launched in July 2016 to give enterprise customers a streamlined, easy-to-manage product that could be used to protect …
We have complimentary equipment like hubs and modems in most modern houses, with two or more computers and Internet connections, which don’t communicate with but assist in maintaining the network. …
Even though they provide Ethernet services, they require wire connectors or Registered Jacks, which come in various configurations and are commonly used in telecommunication exchange companies. Rj10 vs Rj22 RJ10, …
They are made for Layer 2 and Layer 3 switching, which is quite a trend these days among those who use Cisco switches. Cisco LAN Base vs IP Base Cisco …
The world is moving ahead at a serious pace, relying on technology to get everything done. As a result, mobile phones have become one of the most essential tools to …
The rifeness of data transfers nowadays is massive; however, so are the risks of cybercrime. There are a number of serious threats that a business or organization may face while …
BDC or Batch Data Communication and Call Transaction are methods of interfacing strategy. One can run over numerous contrasts between BDC and Call Transaction. The handling is delayed in Batch …
Cisco provides a diverse selection of modular and fixed-configuration switches to help businesses choose the perfect networking solution. These switches assist you in keeping up with the ever-changing dynamics of …
Both rj9 and rj22 are very similar to each other; one can rarely see any difference between them. However, there are a few differences that can be addressed. Like any …
A whole computer network contains and works with a chain of many different things and networks. This work requires two or more two computers with an established network. These networks …
Technology has developed over the years and is still developing at a pace no one could imagine. GSM was one of the first advancements in this field as it enabled …
Transceivers are the modern-day equipment for data transmission. Wireless communication has become an important part of our daily lives. Cisco XFP and SFP are two of the best modules of …
It helps in preventing call systems from being overwhelmed. It also helps in preventing callers from becoming caught in a call loop. PBX vs ACD Private Branch Exchange (PBX) is …
Cisco IOS File System (IFS) is a feature that acts as a single interface for all the files in the system that are available on the routing device. It is …
Both 2 G and 5 G are cellular networks used by people. 2 G was first introduced in the year 1993. The most recent cellular network is 5 G, which …
Cisco is an American multinational company that provides its services in IT and networking. The MSE( Mobility service engine) is a hardware engine, and the CMX is software. Often, these …
Cisco Packet Tracer and GNS3 are two popular network management and simulation programs that may be used to prepare for certification tests or network feature testing without the need to …
Communication is the essential ingredient and backbone of all aspects of the world. From the stone age to the modern day, communication has gone through a sea change. From symbols …
Zscaler and Cisco Umbrella both are considered internet security solutions that protect the integrity of user data and also protect their personal information. In the internet world, it is quite …
Cisco NETCONF and NETCONF-YANG may seem to be the same. They aren’t the same in any way, but they are used at the same level. Both these together help in …
In the contemporary world, cellular phones play very important in everyone’s life. When it comes to the technology of cellular phones, they are mainly portrayed by generations. It is impossible …
The GPS navigation system in our vehicles is familiar to all of us.GPS helps in searching different places and also helps in finding the correct distance from our location to …
In the present scenario, where info and tech are considered necessary for survival in the digital world, the usage of VPN has gained popularity. VPN provides privacy online, which has …
ISE stands for Identity service Engine, and ACS stands for Access Control server. ISE and ACS are both policy-based security servers provided by Cisco. ACS system has been used for …
Valet and Valet Plus by Cisco offer a simpler method to associate your organization gadgets and to get to the Internet easily. You simply need to follow a progression of …
In computer networking and telecommunication, communication cables are the most essential components. These cables transfer data from one unit, maybe a computer or communication unit, to another unit. These might …
In today’s world, where communication through the internet has become the need of the hour, the need for communication software has increased immensely. The quality of software becomes quite important …
LTE stands for Long Term Evolution. It uses orthogonal frequency-division multiplexing (OFDM) with either single-carrier frequency division multiple access (SC-FDMA) or the more popular multi-carrier code division multiple access (MC-CDMA). …
Today’s age is the age of the internet and wireless communication. This revolutionary development has come about because of the advent of multiple tools and devices that offer easy, hassle-free …
In today’s society, Apple iPhones are the status symbol which many people aspire to own. The company provides numerous options for cell phones to cater to the needs of different …
Collision avoidance and Collision-detection are two types of CSMA: Carrier-sense multiple access and a Media Access Protocol (MAC). Here, a node needs to confirm whether there is any kind of …
Computers and technology have become a part of our daily life. Everything is dependent on them. Other things are connected to computers and daily usage. An example of this can …
Science has advanced so a lot, and a lot of things have changed therefore. One thing that has continued as before is the way that nothing is steady. As the …
Today most of the duties and tasks are carried out by the usage of the internet. Several people make the most use of internet access for several purposes. WAP vs …
Modern-day internet facility is very different from that of the past years. Technology has advanced quite a lot in these years. From being able to provide various types of servers …
A certain way or protocol determines the working of a computer network between several devices. The set of rules that are executed so that data broadcasted between several devices in …
Both MPLS and leased lines are related to WAN (Wide Area Networking). These are the connections that are used to transport data across a wide range of populations, but there …
In a network’s design, the network’s brain is the network switch that is used. All the devices are all connected and kept in contact by the networking hardware. Choosing and …
In the epoch of technology, the internet is way more important than a normal man thinks. Especially the need for wifi, mobile data, and other wireless internet providers is burgeoning. …
Technology and inventions are some of the core components that have made the world easier and, overall, faster year by year. In today’s world, people come in confused in the …
For years, the word “Wi-Fi” has been used along with wireless Internet, be it your private home or free Wi-Fi hotspot, accessing cafés, highways, colleges, and so on, virtually wherever …
Staying connected to the internet has become almost similar to basic needs today. This brings us to getting an internet connection that guarantees a consistent and secure data rate. Broadband …
Telephones have been replaced with smartphones. Every person (adult) definitely has a smartphone of his own. Everything can be done on these smartphones from any place in the world. This …
VPN and MPLS are different systems that help you to surf the internet safely. These systems also support improving connection speed and your privacy by keeping you more anonymous. These …
As technological advances take place, wireless technology becomes more popular among netizens. Without direct or wired connectivity, the transfer of files and data from one device to another requires the …
The third generation of cell phone technology is referred to as 3G. Rather than being a single standard, 3G is a set of innovations that provide the same quality of …
Similar to Airtel, Jio, and other networks in India, Verizon and Sprint are two of the popular telecommunication networks in America. Verizon vs Sprint Verizon is a wireless telecommunication corporation …
The traffic on the internet is increasing day by day. Internet providers are always looking for new, advanced, faster, secure, and easy-to-access options for their customers so that their experience …
We need a particular sort of interface between the nodes to connect devices and transfer data. So far, this is being achieved by two legendary data-transferring mediums: the Ethernet and …
We all are caught on the net now, the internet. Life is immovable without the internet. And even though we are not bothered about the internet’s technicalities, a few terms …
A registered jack (RJ) is a normalized telecom network interface for associating voice and information hardware with assistance from a nearby trade transporter or significant distance transporter. Likewise, enrolled jacks …
With the rise of modernization as ever, where nobody can feel connected without the internet, Wifi Modem and Wifi Routers are some of the easiest and most common ways to …
The figures Hub and Spoke, and Point to Point are models used in the airlines’ networks and transportation industry. The Hub and Spoke Model connects the airlines from two points …
The world has changed from only physical access to wholly digitalized. Everything has become digitalized, from the local vendor to the high-maintained shop owner. NIPRNet vs SIPRNet NIPRNet is used …
Everything is going wireless, but to make it wireless, we need wires. Wires are mainly required when it comes to telecommunication or computer networking. RG11 is a thick cable that …
Registered Jacks are abbreviated as Rj, and the number is assigned per its physical characteristics. Bell Laboratories first discovered these in 1973. Registered jacks have many telecommunication applications; they connect …
RJ 12 and RJ14 are two separate models in structured cabling. RJ, a registered jack, is a connector mainly made and used in networking applications. The name ‘Jack’ applies to …
RJ stands for Registered jack, a female-type connector used for system cables, wiring, and manufacturing jacks. A registered jack’s main purpose is to connect various telecom devices and data tools …
Telecommunication was once used in households and workspaces, but now the use of telephones has become limited. Although they provide Ethernet services, they require wire connectors or Registered Jacks, which …
Most people can quickly distinguish each cable’s variations and unique usage between an RJ11 and RJ45. But it’s a bit tougher regarding an RJ45 and an RJ48. The modular connector …
A registered jack (RJ) is a standard network interface used in network cabling, wiring, and jack design. The essential capacity of registered jacks is to interface distinctive information hardware and …
A registered jack (RJ) is a generic telecommunications network interface that connects voice and data equipment to a local exchange or long-distance carrier service. Registered jackets are designated primarily by …
The rj12 and rj45 are made of plastic material used for a connector. Cable and connectors play a tremendous part in our lives. We may keep jumping on our television …
A registered jack is a standardized network interface used as an interface in telecommunication networks to a local exchange carrier service or a long-distance service carrier. The commonly registered jack …
In the past two decades, technology has taken a wide leap forward. Social media, artificial intelligence and smartphones became a hot topic in the 2010s, and we have thrived in …
All know the importance of mobile and its network in this era of IoT. Mobile can now do anything that was next to impossible in the early 90s and 80s. …
Technology has evolved from its beginning televisions was enclosed in wooden boxes with the smallest screen. The worst audio quality evolved into the best smart televisions with the highest quality …
QAM and ATSC are two digital standards that play an important role in receiving and decoding the digital signals that Television stations and cable companies send. QAM stands for Quadrature …
Modern-day means modern technology and modern technology means a rapid increase in various electrical demands. The different digital needs require new items now and then. The words RJ45 and CAT5 …
Because of its high access speeds, broadband internet service is today’s most used form of Internet access. Broadband Internet networks improve over conventional dial-up methods, with far faster data communication …
3G (Third Generation) technology provides relatively slower data speeds compared to LTE (Long-Term Evolution), ranging from 0.1 to 2 Mbps. LTE, on the other hand, offers significantly faster data rates, …
SNMPv2 offers basic security features like community strings for authentication, while SNMPv3 provides robust security mechanisms such as encryption, authentication, and access control, enhancing confidentiality and integrity of network management …